SKIP your way to security
How does Sun's Simple Key Management for IP provide 3 levels of network security? We show you how to install SKIP and build an encrypted channel between Solaris hosts
|
|
SKIP your way to securityHow does Sun's Simple Key Management for IP provide 3 levels of network security? We show you how to install SKIP and build an encrypted channel between Solaris hosts
|
Sun's SunScreen SKIP for Solaris creates data encryption and/or authentication between two or more hosts across an IP network. We examine the step-by-step process of how it functions to provide three levels of security and take you through its installation. (3,500 words)
|
Mail this article to a friend |
There are few occasions more embarrassing for a computer professional than having his or her password sniffed from the network by the computer hack down the hall. You may have encountered this situation before -- unbalanced Unix guy in the next cubicle runs a packet capture program, lifts your password sent in the clear during your telnet session, then approaches you with a line something like "Bet I can guess your password!" Or worse, shows it to your project leader.
While this situation may be office fun and games, it does illustrate the potential vulnerability inherent in sending your password or sensitive information over the network in this age of client/server computing and remote access. And although your organization may have superb network and system administration, realize that by compromising just one system on your local network a hacker could potentially create a listening post for passwords and other information flying over the network in clear-text form.
Do you live fear at the beginning of every remote login or FTP session? Who might be listening or capturing packets? Has a nearby system been comprised? Should I be paranoid and change my password after using the network? Fortunately, there are now low-cost commercial solutions for secure host-to-host communication, including a nifty tool from Sun called Simple Key management for IP, or SKIP.
SKIP applications
Sun's SunScreen SKIP is a software module that creates encrypted,
authenticated point-to-point (unicast) or point-to-multipoint
(multicast) channels between two or more hosts connected over an IP
network. Presently, SKIP is available for the Solaris, SunOS, and
Windows 95 platforms.
Sun recently surprised the industry with its announcement that it will sell 128-bit encryption software from Russian company Elvis+ in both U.S. and international markets (See Resources for link to our news story.) The Elvis+ software, sold under the name SunScreen SKIP E+, will be available for Windows 3.x, Windows 95, and Windows NT platforms in August. Chris Tolles, Sun's SKIP product manager, says Sun has not yet decided whether it will license Elvis+ encryption software for Solaris. However, Sun will be introducing its own version of SKIP for Windows NT soon, and a JavaOS variant of SKIP is also in the works, he says.
SKIP can be used to enhance security in any environment but is especially useful when a site firewall may not exist or would be difficult to implement (like at a university or a large laboratory research campus or in environments where there exists a need for hosts behind a firewall to communicate securely over the Internet). Listed below are some example uses of SKIP:
|
|
|
|
|
SKIP's multilevel security
SKIP provides three levels of network security.
The first is authorization control. This means that you can use SKIP to control which systems or networks are permitted (or authorized) to send packets to the SKIP host. SKIP implements authorization using access control lists (ACLs). It is a snap to add and delete system names and network numbers to the SKIP ACL using the graphical management tool. (More on this tool later.) SKIP also has an optional mode where it will prompt the user whenever a remote system not in the ACL attempts to send a packet. This feature is useful if you forget to add a system after initial SKIP installation or are just curious as to what other systems are trying to send you packets.
The second level of SKIP security is data authentication. Authentication is the process of verifying that data sent by a remote system truly originated from that system and that the data received was not altered in any way from the time it left the sending system. This is also referred to as data integrity. SKIP authenticates every packet using the Hashed MD5 authentication algorithm and gives you the option of enabling or disabling authentication for each secure channel you create.
The third and final level of SKIP security is encryption. Encryption protects the privacy of data that is sent over a network connection by encoding it in a scrambled format that only the sender and receiver can decode. Anyone who is listening on the network and intercepts your packets will not be able to interpret them unless they have considerable time and computing power at their disposal.
Flavors of SKIP
SKIP is quite flexible in the number of encryption algorithms and
key lengths it supports. SKIP uses the Diffie-Hellman key agreement
protocol to encrypt the master key or packet-encrypting key. Public
key lengths of 512, 1024, and 2048 bits are available and can
optionally be authenticated through the use of X.509 certificates.
Packet data is encrypted using one of several standard symmetric algorithms that SKIP supports. These include 40-bit RC2, 40-bit RC4, 56-bit DES, 56-bit Triple-DES, and 128-bit SAFER. Algorithms and key lengths can be configured on a per host-pair basis. (For those needing a primer on security technology in general and encryption algorithms in particular, the RSA FAQ listed in Resources below is a good starting point.)
The combination of key lengths and encryption algorithms you select will depend in part on the security needs of your application or environment and whether the use of SKIP will be domestic-only (includes Canada!), export-controlled (overseas offices of U.S. corporations or subsidiaries), or global (unrestricted use). The table below summarizes the versions of SKIP, the supported algorithms and key lengths, and U.S. list pricing:
| Version of SKIP | Public Key | Encryption Algorithms | Authentication | US List Price |
|---|---|---|---|---|
| Global | 512-bits | 40-RC2/40-RC4 | Hashed MD5 | $99 |
| Export-Controlled | 1024-bits | 40-RC2/40-RC4/56-DES | Hashed MD5 | $124 |
| Domestic-Only | 2048-bits | 40-RC2/40-RC4/56-DES/56-3DES/128-SAFER | Hashed MD5 | $149 |
How SKIP works
SKIP software runs as a kernel process that can be visualized
sitting between the network interface of the host system and the IP
protocol software layer. Residing above IP is the TCP or UDP
transport layers and then the application layer. A simple, layered
view of a SKIP host is shown below:
| The User |
| Application Layer |
| TCP/UDP Protocol Layer |
| IP Protocol Layer |
| SKIP Software |
| The Network Interface |
| The Network |
Note that the presence and operation of SKIP is transparent to the user, the applications, and the TCP/IP software layers. SKIP requires no modifications to the existing IP software or base of applications in order to perform encryption. A packet is assembled down through the layers in the same way it would without the presence of SKIP. However, instead of the IP layer handing the packet to the network interface for transmission over the network, the SKIP software intercepts the packet and performs encryption and/or authentication as needed.
So what is SKIP doing to the packet before sending it over the network? First, it is looking at the destination address of the packet and then checking the ACL to determine if the packet should be encrypted, and if so, what algorithm to use. Similarly, SKIP checks to see if data authentication is required for the secure connection to the destination host.
If required by the ACL, SKIP will perform data encryption and/or authentication and then build its own custom header to prepend to the packet. (Note that if the ACL does not specify encryption and/or authentication for the destination host, then SKIP will simply pass the packet to the network interface without further processing.) The SKIP header will contain parameters specific to SKIP, such as the SKIP version number, the encryption and authentication algorithms used (since SKIP supports several), and the all-important packet encryption and authentication keys. The SKIP header contains several other fields and is actually more complex than presented here. For those who desire to know the detailed format and function of the SKIP header, Sun has published the SKIP specification as an Internet Draft Standard. (See Resources below for link to the SKIP spec.)
Shown below is a simplified view of the SKIP header prepended to the original packet:
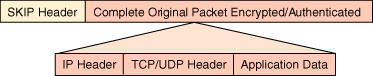
The final step in the process of building a complete SKIP packet is the prepending of yet another header, in this case a standard IP header. This final header is a conventional IP header that allows the SKIP packet to traverse routers and the Internet as any other IP packet would. There is a minor difference compared to most packets. The IP header produced by the SKIP software has a PROTOCOL field value of 57, which is the unique value assigned by the Internet Assigned Numbers Authority (IANA) to identify the SKIP protocol as the next higher protocol. Normally this field will have a value that corresponds to the TCP or UDP protocol as the next layer up in the protocol stack. The SKIP packet needs its own protocol number because the next header of the packet is a custom SKIP header and not a conventional TCP or UDP header.
Shown below is the final packet produced by the SKIP kernel software that is handed down to the network interface for transmission over the network:
| IP Header | SKIP Header | Complete Original Packet Encrypted/Authenticated |
Upon being received by a remote SKIP host, the packet is delivered from the network interface to the SKIP software. SKIP then examines the PROTOCOL field of the IP header. If the protocol number is 57, then SKIP will proceed to decrypt and/or authenticate the packet as necessary. If the protocol number is a value other than 57, then SKIP hands the packet to the next higher layer specified (usually TCP or UDP). Note that packets originating from a SKIP host will not always have the custom SKIP header and protocol number 57. If the ACL on the sending SKIP host specifies that packets to the destination host should not be encrypted or authenticated, then the SKIP host sends a standard packet.
This, in a nutshell, is the basic packet-level operation of SKIP. It is important to realize that, although SKIP attaches a custom header on packets destined for hosts that require secure communication, the final packet transmitted over the network is a standard IP packet. This standard IP design makes SKIP flexible and transparent, and allows SKIP-encrypted packets to travel around your local network or over the Internet unaffected by intervening routers.
Building a secure channel
Let's look at a quick example of how to install SKIP and create an
encrypted channel between two Solaris hosts. In general, it is
relatively easy to work with SKIP, especially the GUI-based tool
used to enter the parameters of the secure connection. SunScreen
SKIP for Solaris 1.0 was used for the purposes of this article.
SunScreen SKIP 1.1 is the current version, but there are no
significant differences between the two products.
The installation of SKIP is a basic Solaris package installation from CD-ROM. If you ordered the export-controlled or domestic-only versions of SKIP, a second CD-ROM is included for adding the stronger encryption algorithms and public-key lengths. System requirements are minimal and consist of any SPARC or x86 workstation running Soaris 2.4 or higher with 16 megabytes RAM and six megabytes free hard disk space.
After the SKIP packages are installed on the two host systems that
will be communicating securely, you are ready to create the secure
channel. NOTE: This discussion will focus on using Unsigned
Diffie-Hellman (UDH) keys because it is the fastest and easiest way
to get SKIP working in your environment. If your applications or
organizational security policy will require the use of signed
certificates for the DH keys, then you can always go back and add
self-signed or CA-signed X.509 certificates using SKIP's
skipca and skipdb commands. These
utilities are covered in the SKIP documentation and SKIP man pages.
In this example, unsigned DH keys will be used.
The first step in creating the secure channel is to generate the UDH
key pairs on both SKIP hosts using the skiplocal
command as the root user. Once the key pairs are created, the public
key component of the pair on each host must be transferred to the
other host. This is probably the most cumbersome part of the whole
process, but SKIP makes it easier by including a command that not
only generates the public key in ASCII format, but outputs the
entire command syntax required to enter the public key and UDH
certificate on the other SKIP host. Thus, you can simply copy and
paste this output between text windows open on both hosts. If you
are building a secure channel between hosts that are geographically
separated or perhaps reside in different organizations, you can pipe
the ASCII output into mail and send it off to the remote host
administrator for installation.
After the UDH public keys have been exchanged on the SKIP hosts, the
next step is to specify the parameters of the secure channel.
Although you can configure the channel using SKIP's command line
interface (CLI) utilities, it's much easier to use the graphical
management tool, skiptool. Simply start
skiptool in the background as the root user, and you
are ready to begin the configuration of SKIP.
The skiptool interface basically consists of two
columns, one column being an ACL for remote systems you allow to
communicate with the SKIP host (authorized systems) and the other
column being an ACL for those remote systems that are not permitted
communication. If SKIP does not come pre-configured with an entry
called "default" in the authorized systems' ACL column, you should
add it immediately. (First Customer Ship versions of SKIP omitted
this important entry.) The "default" entry allows the SKIP host to
function as it did prior to the SKIP installation, communicating in
the clear with all other remote systems. From this initial
permissive state, you can then begin to add secure channels and
reject packets from certain remote hosts or networks.
To begin entering channel configuration paramenters, use the
pull-right "Add" menu on the skiptool interface and
select Add -> Host -> SKIP. The image below shows the "skiptool"
interface, the "default" entry, and the pull-right menu selection
for adding a secure channel to another host system.
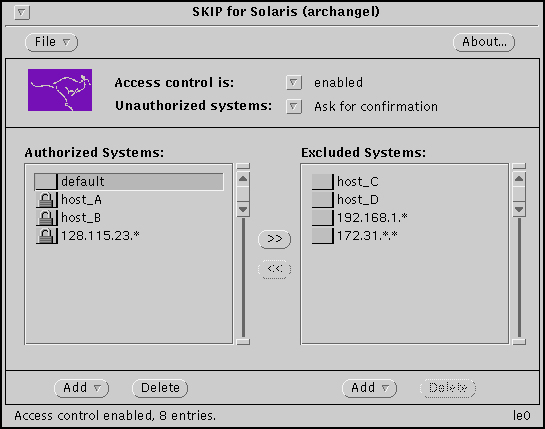
Choosing the Add -> Host -> SKIP menu selection results in a pop-up dialog box that can be used to enter encryption and authentication parameters. The fields in the dialog box that need to be populated with values for creating a basic secure channel are the "Hostname", "Key encryption," "Traffic encryption," and "Authentication" fields. SKIP will automatically display as options the encryption algorithms that correspond to the version of SKIP you purchased. Once you have entered the values into the dialog box, click the "Apply" button and then choose the menu selection "File -> Save" to permanently save the channel configuration. NOTE: The other fields in the dialog box pertain to features not covered in this article. The SKIP documentation and online man pages cover these parameters in more detail.
Using SKIP
The operation of SKIP on your host system is transparent and after
you create secure channels, SKIP works silently to authorize,
encrypt, and authenticate packets according to the ACL entries you
have specified. However, it is possible to get an idea of what SKIP
is doing by using the various statistical utilities that come with
SKIP.
With SKIP, you view operational statistics in the following five areas:
Statistical reports can be viewed by pulling right on the "File"
menu in the skiptool and selecting a report category.
SKIP stats consist mostly of operational counts, such as the number
of packets encrypted or the number of authentication errors. The
reports are interesting to view periodically to get a snapshot of
the work that SKIP is doing. There are also CLI-equivalent versions
of the SKIP statistical reports you can run. The CLI versions
are useful for saving or printing the output of a report.
Final analysis
SKIP has many positive qualities. In summary, some particularly favorable elements include:
skiptool interface
SKIP's documentation, however, is a little disappointing. Even though I was reading through a First Customer Ship (FCS) version of SKIP, the typos and lack of explanatory information at times was very apparent. Other minor deficiencies of SKIP include the inability to work with certificates in the GUI tool and the lack of a SKIP AnswerBook. Also, the (current) limited platform availability of SKIP may be a concern to those with multivendor Unix and Macintosh environments.
Nevertheless, SKIP overall is a well-designed and useful security tool for Sun and PC environments. The configuration and use of SKIP is made easy by the graphical management tool. The positioning of SKIP as an open, Internet standard should encourage other vendors to adopt the specification and develop products that use the SKIP protocol.
A final note worth mentioning is that although this article
presented the basic configuration, operation, and use of SKIP, there
are several other features of SKIP that you may find useful for your
environment. Other features include secure multicast capability,
support of mobile users, and the ability to specify tunnel
parameters for forwarding through a firewall. These topics were not
addressed in order to keep the length and scope of this article
within sane limits. However, further information on these features
is available in the SKIP documentation or from the Sun Internet
Commerce Group that developed and supports SKIP.
![]()
|
|
Resources
About the author
Ken Masica is an electrical engineer specializing in the areas of
network design, simulation, and security.
Reach Ken at Ken.Masica@sunworld.com.
If you have technical problems with this magazine, contact webmaster@sunworld.com
URL: http://www.sunworld.com/swol-06-1997/swol-06-skip.html
Last modified: